

Certified Information Systems Security Professional (CISSP) Training in Brisbane
The Most Comprehensive Certification Course for Guaranteed Career Success
30K+ Enrolled


CISSP, Certified Information Systems Security Professional, is a cybersecurity certification for experienced professionals. Security managers, practitioners, and executives opt for CISSP Certification Training to advance their careers. The certification will help you take cybersecurity more seriously, leading to a higher salary, competitive edge, and ability to protect communities and businesses from cyber dangers.
Read more...


Guranteed to Run Workshops

Expert-Led Study Sessions

Networking Opportunities

Flexible Monthly Payment Plans

Real-World Case Studies

Hands-On Project Experience
450K+
Professionals trained
250+
Workshops every month
30+
Trainers
450K+
Professionals trained
250+
Workshops every month
20+
Trainers
The Certified Information Systems Security Professional (CISSP) is the most recognized certification in the information security industry. CISSP certification provides technical and managerial expertise in designing, engineering, and managing their knowledge and career in information security programs. It covers eight key domains, including security, risk management, network security, and software development security, ensuring a well-rounded understanding of cybersecurity. The CISSP Common Body of Knowledge (CBK) remains across various industries, providing the certification's applicability to all areas of information security. It was the first security credential to meet the stringent ANSI/ISO/IEC Standards1702.
The CISSP certification validates expertise in designing, implementing, and managing a robust cybersecurity program. It is ideal for security professionals, managers, and executives, such as CISOs, security analysts, security consultants, and IT directors, who wish to enhance their professional standing and demonstrate their commitment to maintaining a secure business environment.
Simpliaxis provides comprehensive online CISSP training to help professionals thoroughly prepare for the CISSP exam. The course includes practical training and real-world case studies, prepares participants for the exam, and helps them obtain the CISSP certification. Simpliaxis ensures professionals are well-equipped to excel in their cybersecurity roles.
Excellent
30K++ Enrolled
Course Overview
The Certified Information Systems Security Professional (CISSP) is the most recognized certification in the information security industry. CISSP certification provides technical and managerial expertise in designing, engineering, and managing their knowledge and career in information security programs. It covers eight key domains, including security, risk management, network security, and software development security, ensuring a well-rounded understanding of cybersecurity. The CISSP Common Body of Knowledge (CBK) remains across various industries, providing the certification's applicability to all areas of information security. It was the first security credential to meet the stringent ANSI/ISO/IEC Standards1702.
The CISSP certification validates expertise in designing, implementing, and managing a robust cybersecurity program. It is ideal for security professionals, managers, and executives, such as CISOs, security analysts, security consultants, and IT directors, who wish to enhance their professional standing and demonstrate their commitment to maintaining a secure business environment.
Simpliaxis provides comprehensive online CISSP training to help professionals thoroughly prepare for the CISSP exam. The course includes practical training and real-world case studies, prepares participants for the exam, and helps them obtain the CISSP certification. Simpliaxis ensures professionals are well-equipped to excel in their cybersecurity roles.
CISSP Certification Training Training Highlights
Instructor-led CISSP Training
40 Hours of in-depth learning sessions
Hands-on practical experience
Lab time as per (ISC)2
Demos & Projects
Real-life simulations based learning

Career upliftment

Chief Information Security Officer (CISO)
Director of Security
Information Security Analyst
Security Manager
IT Director
Security Consultant
Security Architect
Security Auditor
Security Systems Engineer
Network Architect
Benefits focused on Individuals and corporate
Common attendees

Prerequisites for CISSP Certification Training certification training
COURSE Curriculum
40+ Certification programs made an impact
Employee retention improved by 45%
Work satisfaction and capabilities improved by 30% on an average
100+
Clients













CISSP Certification Training Certification COURSE For Corporates
Simpliaxis provides In person and live virtual instructor- led corporate training program customized for enterprise teams who wish to train their employees on specific aspects of their job processes or responsibilities. The corporate training by our expert certified trainers will enhance your learning curve and enable your teams to utilize their skills to meet the industry standards
Our Customer words for us


















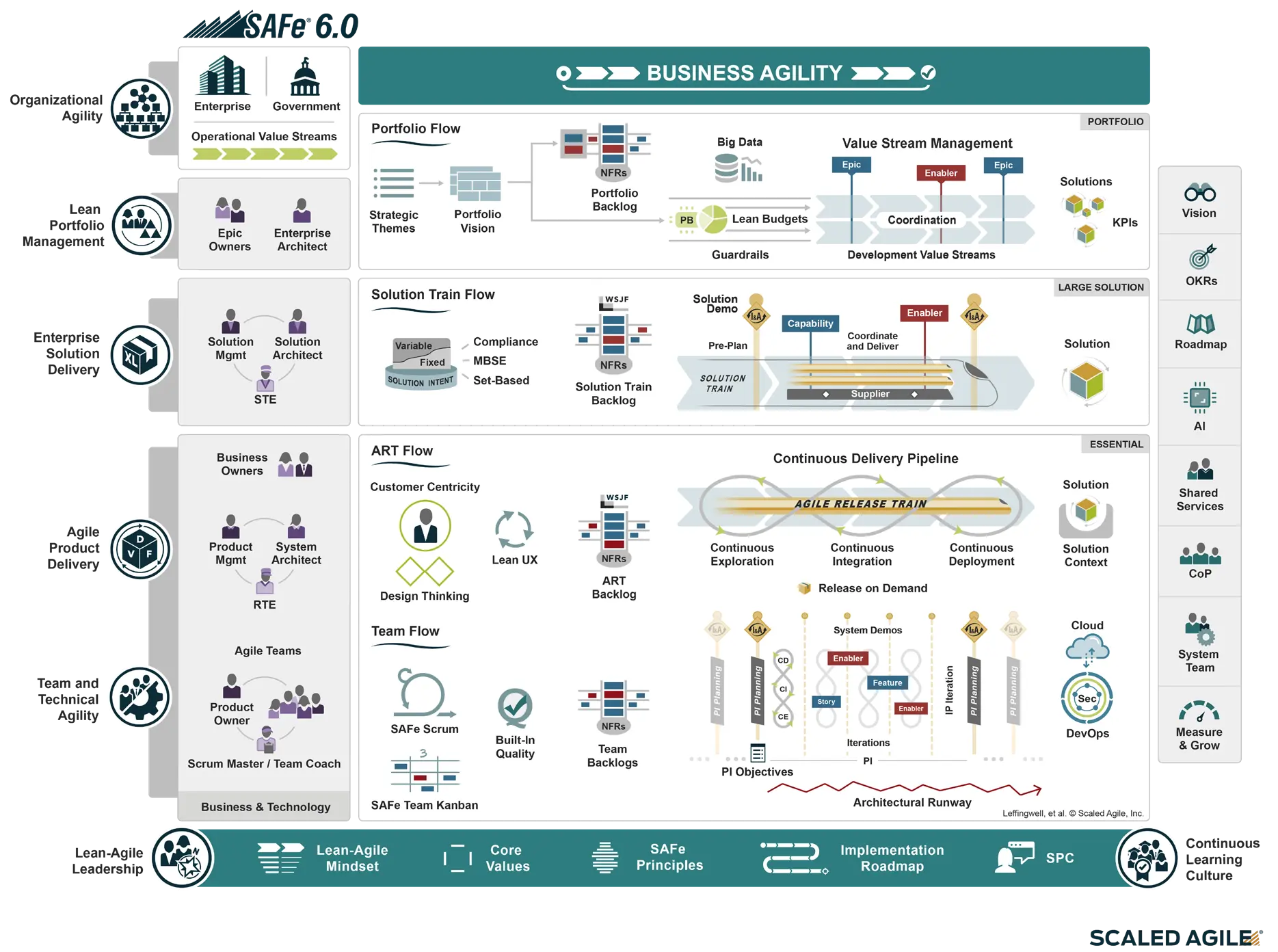
SAFe Big Picture
- Achieving Business Agility with the Scaled Agile Framework (SAFe)
Meet the Team That's Invested in Your Success
Instructors
View All TrainersCISSP Certification Training Course FAQs
The eight domains of CISSP are:
With a CISSP certification, you can pursue roles such as:
Numerous respected organizations hire CISSP professionals:
During the CISSP course, you will acquire advanced skills in:
You can reach out to our experienced career counselor
or email us on support@simpliaxis.com
or contact any of our phone numbers
or you can chat with us anytime
or visit our contact us page https://www.simpliaxis.com/contact-us